Windows WannaCry Ransomware Security Advisory
Description
Originally Published May 12, 2017
Last Update: May 15, 2017
A massive ransomware campaign hit computer systems of hundreds of private companies and public organizations across the globe – which is believed to be the most massive ransomware delivery campaign to date.
While the University of Regina has not been impacted yet, be aware that the risk is high.
It is belived that emails with this ransomware may have subject lines such as:
– Copy_[with Random Numbers],
– Document_[with Random Numbers], Scan_[with Random Numbers],
– File_[with Random Numbers]
– PDF_[with Random Numbers]
This is not an exhaustive list. Please be extra cautious and do not open any emails that seem suspicious or unfamiliar no matter what the subject line is.
The Ransomware in question has been identified as a variant of ransomware known as WannaCry (also known as 'Wana Decrypt0r,' 'WannaCryptor' or 'WCRY').
Like other ransomware variants, WannaCry also blocks access to a computer or its files and demands money to unlock it.
Impacted users will see a screen similar to the following:
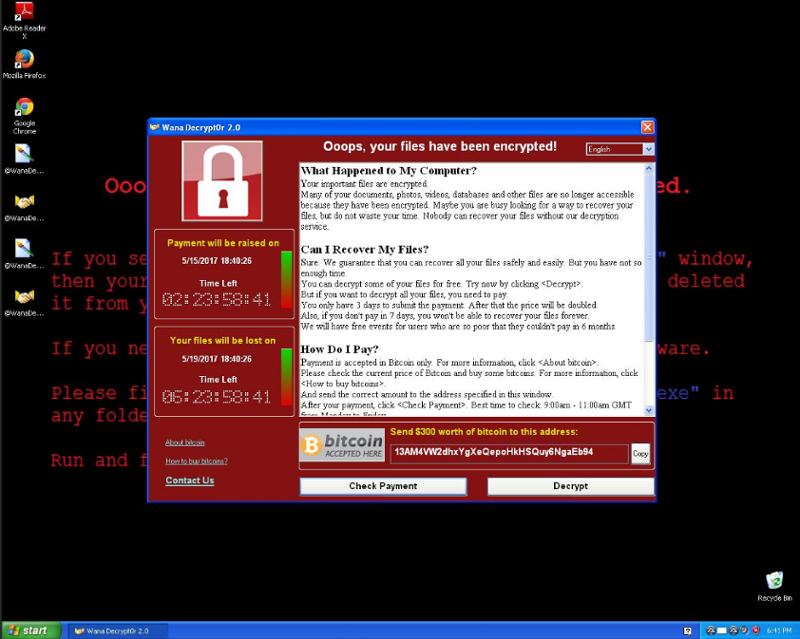
Impact
Once a single computer in is infected by the WannaCry ransomware, the worm looks for other vulnerable computers and infects them as well.
Microsoft released a patch for the vulnerability in March (MS17-010), but many users and organizations who did not patch their systems are open to attacks. University of Regina managed computers should have received this patch automatically.
The exploit has the capability to penetrate into machines running unpatched version of Windows XP through 2008 R2 by exploiting flaws in Microsoft Windows SMB Server. This is why WannaCry campaign is spreading at an astonishing pace.
Impacted platforms:
– Windows XP, Windows 2003 (see https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/)
– Windows Vista with Service Pack 2 x86 KB4012598
– Windows Vista with Service Pack 2 x64 KB4012598
– Windows Server 2008 with Service Pack 2 x86 KB4012598
– Windows Server 2008 with Service Pack 2 x64 KB401259
– Windows 7 with Service Pack 1 x86 KB4012212 or KB4012215
– Windows 7 with Service Pack 1 x64 KB4012212 or KB4012215
– Windows Server 2008 R2 with Service Pack 1 KB4012212 or KB4012215
– Windows 8.1 x86 KB4012213 or KB4012216
– Windows 8.1 x64 KB4012213 or KB4012216
– Windows Server 2012 KB4012214 or KB4012217
– Windows Server 2012 R2 KB4012213 or KB4012216
– Windows 10 x86 KB4012606
– Windows 10 x64 KB4012606
– Windows 10 version 1511 x86 KB4013198
– Windows 10 version 1511 x64 KB4013198
– Windows 10 version 1607 x86 KB4013429
– Windows 10 version 1607 x64 KB4013429
– Windows Server 2016 KB4013429
Resolution
Ensure you Windows machines are full patched and upto date. If you haven't patched your Windows machines and servers against EternalBlue exploit (MS17-010), please do so as soon as possible. This patch is available at Microsoft Security Bulletin MS17-010. Machines such as Windows XP/2003, which are off support and do not recieve security patches normally, have been provided a patch for this issue. Given the potential impact, Microsoft made the decision to make the Security Update for Windows XP, and Windows Server 2003, broadly available for download. If you run these operating systems, please see download and install the patches from Microsoft.
If patches are not available for a system and it cannot be protected via alternative controls, such as anti-malware, then it is recommended that SMB ports (139, 445) be blocked for the system until such time as it can be patched or additional controls applied to protect against infection.
To safeguard against such ransomware infection, you should always be suspicious of uninvited documents sent an email and should never click on links inside those documents unless verifying the source.
Ensure that your documents are backed up. This means ensuring they are stored on a network drive or an external storage device that is not always connected to your PC.
Moreover, make sure that you run an active anti-virus security suite of tools on your system, and most importantly, always browse the Internet safely.
If you are impacted, contact the IT Support Centre.
Resources
External Resources:
Customer Guidance for WannaCrypt attacks (Microsoft Patches for Windows XP/2003)
What you need to know about the WannaCry Ransomware? (Symantec Security)
Massive ransomware infection hits computers in 99 countries (BBC)
Ransomware Scam (Canadian Anti-Fraud Centre)
Massive Wave of Ransomware Ongoing (ISC)
Ransomware Hits (Malwarebytes)
Internal Resources:
See the Malware Resources page.
Please contact the IT Support Centre if you require assistance:
In person at ED 137 or Archer Library Main Floor Commons

