Information Security Advisories
Learn more about the most recent IT threats to the University of Regina community by viewing the following information security advisories:
Phishing AttemptDATE ACTIVE:11/15/15 THREAT LEVEL:Low TYPE:Credential Phishing |
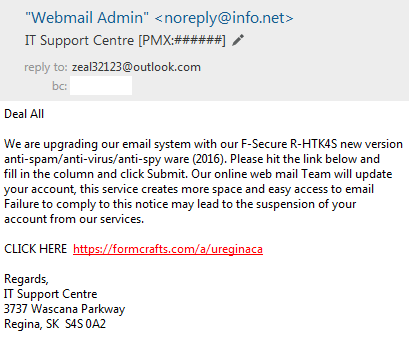
Description: An email claiming to be from University of Regina IT Services is attempting to trick you into giving away your account information. The email will appear similar to:
This email can be recognized as a phishing attempt as it links to a web address that is not at uregina.ca. This email can be recognized as a phishing attempt as it was not sent by a uregina.ca email address. This email can be recognized as a phishing attempt as the University of Regina will never require you to provide information in order to keep your email account. This email can be recognized as a phishing attempt as the University of Regina will always provide a contact person, including name, position and phone number. Impact: Clicking the link and entering credentials will lead to your account being compromised. Resolution: If you did not click the link, delete the email. If you clicked the link and entered your password, change it immedaitely. Resources: |
XCodeGhost
DATE ACTIVE:11/04/15 THREAT LEVEL:Low TYPE:iOS Malware (Trojan) |
Description: Mobile devices running iOS with the XcodeGhost are present on the University network. These devices have been infected with malware from infected apps from the iTunes Store. Devices include iPods, iPads, and iPhones. Impact: Apps infected with XcodeGhost collect the following data from users’ devices:
iOS apps can receive commands from the attacker through the command and control server to perform the following actions:
Resolution: iOS users should immediately uninstall any infected iOS app listed here on their devices, or update to a newer version that has removed the malware. Resetting your iCloud password, and any other passwords inputted on your iOS device, is also strongly recommended as a precautionary measure. Resources: |